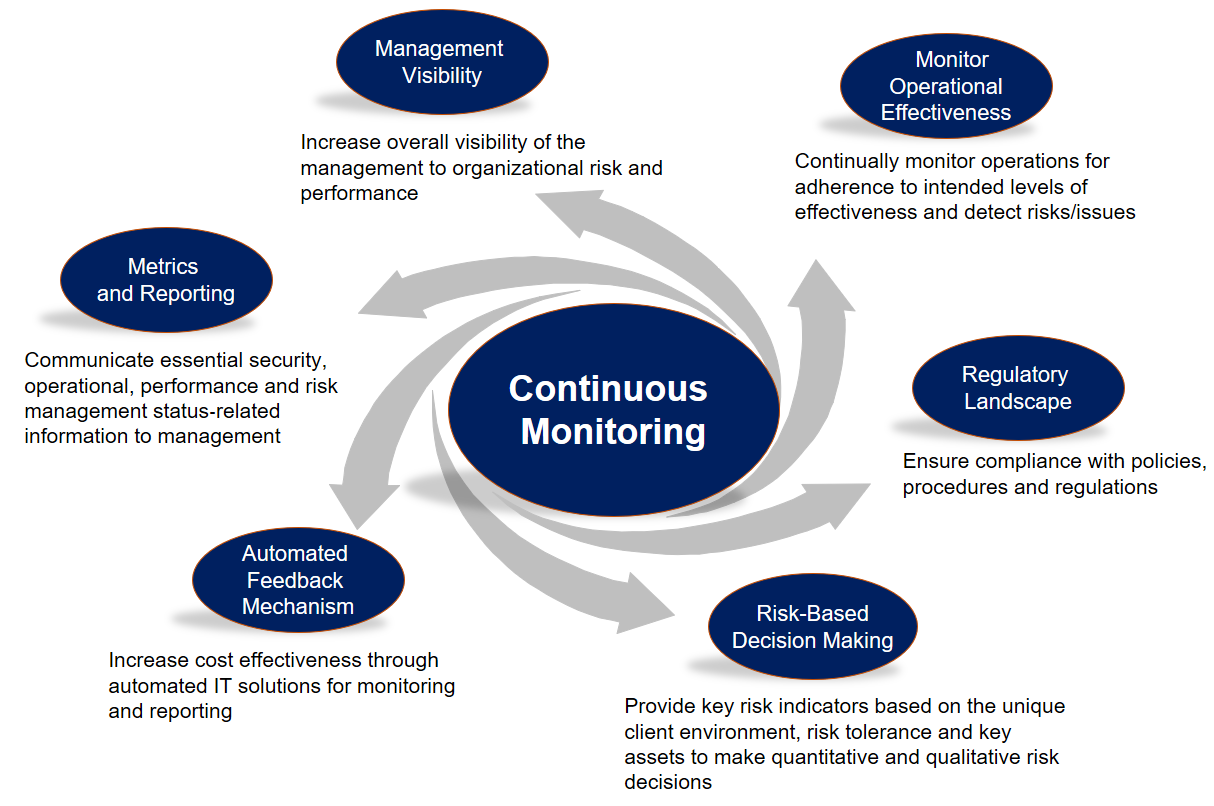
Security Monitoring Process . Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats.
from www.capszen.com
Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats.
Monitoring & IT Security CAPZEN TECHNOLOGIES
Security Monitoring Process The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and.
From www.securigard.ie
Alarm Monitoring Process Securigard House Alarms Dublin Security Monitoring Process Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Learn 5 components. Security Monitoring Process.
From www.corporatecomplianceinsights.com
Compliance Monitoring A Strategic Approach to Monitoring for Compliance Security Monitoring Process Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other. Security Monitoring Process.
From www.thesecuritybuddy.com
A Guide To Database Activity Monitoring (DAM) The Security Buddy Security Monitoring Process Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to. Security Monitoring Process.
From www.neumetric.com
Cyber Security Monitoring What Is It And Why Do You Need It? 2024 Security Monitoring Process The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Continuous security monitoring (csm) is a threat intelligence approach that automates the. Security Monitoring Process.
From www.neumetric.com
Digital Security Monitoring Enhancing Cybersecurity Through Security Monitoring Process Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. The intent of this article is to outline a process to define a. Security Monitoring Process.
From www.yash.com
Operational Technology (OT) Security YASH Technologies Security Monitoring Process Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance. Security Monitoring Process.
From www.aykira.com.au
Security Event Logging, why it is so important Aykira Solutions Security Monitoring Process Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Continuous monitoring is. Security Monitoring Process.
From www.splunk.com
Security Monitoring Splunk Security Monitoring Process Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security. Security Monitoring Process.
From www.cpomagazine.com
Maintaining Security by Monitoring System Health CPO Magazine Security Monitoring Process Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan. Security Monitoring Process.
From www.esds.co.in
How to Prevent Data Breaches with Cyber security monitoring services? Security Monitoring Process Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Security monitoring is an automated process of collecting security data that indicate. Security Monitoring Process.
From middleware.io
What Is Log Monitoring? A Detailed Guide (Updated) Middleware Security Monitoring Process Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security. Security Monitoring Process.
From industrialnews.co.uk
Monitoring cyber security Industrial News Security Monitoring Process Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. Continuous monitoring is an approach where an organization constantly monitors its it systems. Security Monitoring Process.
From www.clearnetwork.com
What is Cybersecurity Monitoring and Why Do You Need It? Security Monitoring Process Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other cyber threats to support. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Learn 5 components your security team should consider when putting together a continuous. Security Monitoring Process.
From www.sentrysecurity.net
Safeguard Yourself with Professional Security Monitoring Services Security Monitoring Process Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous monitoring is. Security Monitoring Process.
From www.proftesting.com
Test Security Flowcharts Professional Testing Blog Security Monitoring Process Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and. Security Monitoring Process.
From www.proftesting.com
Test Security Flowcharts Professional Testing Blog Security Monitoring Process The intent of this article is to outline a process to define a standard operational report for use cases to identify, monitor and respond to incidents and identify several security. Learn 5 components your security team should consider when putting together a continuous cyber security monitoring plan to monitor the threat landscape. Continuous monitoring is an approach where an organization. Security Monitoring Process.
From www.monarchconnected.com
What is Continuous Security Monitoring? Security Monitoring Process Network security monitoring (nsm) is the process of analyzing network traffic to identify suspicious activities and potential threats. Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Learn 5 components. Security Monitoring Process.
From intecit.com
Managed Services Remote Monitoring & Management CybersecurityIT Security Monitoring Process Continuous monitoring is an approach where an organization constantly monitors its it systems and networks to detect security threats, performance issues, or. Security monitoring is an automated process of collecting security data that indicate potential security threats, delivering and. Continuous security monitoring (csm) is a threat intelligence approach that automates the monitoring of information security controls , vulnerabilities, and other. Security Monitoring Process.